System and Security Info iOS Application
SektionEins has released System and Security Info in the iOS AppStore to show processlists in iOS and detect compromised iPhones.
SysSecInfo - System and Security Info

SektionEins is proud to announce the immediate availability of our "System and Security Info" application on the Apple AppStore.

This app shows detailed information about your device and about the running processes from a security point of view.
Features include:
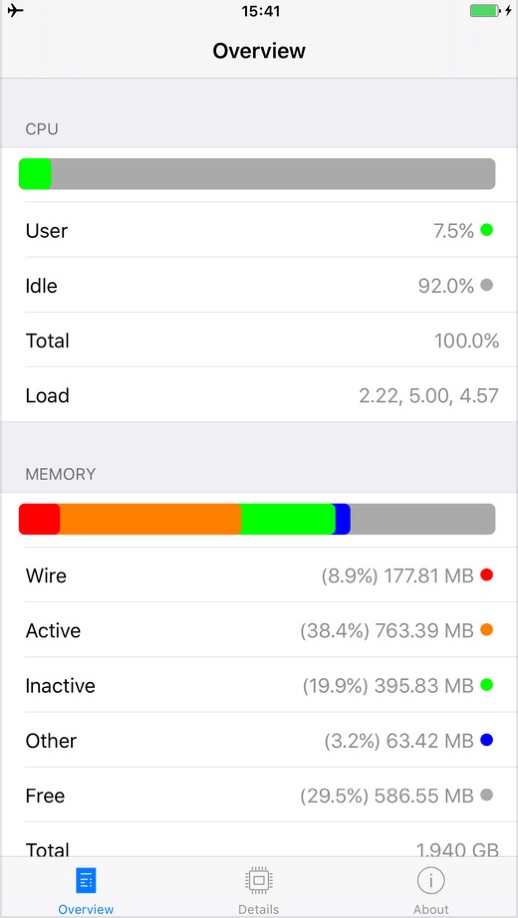
CPU usage
Memory usage
Disk usage
Process list
Inspect running apps: SHA1 Hash, Signature, Entitlements
Jailbreak detection
Security anomaly detection
Malware detection
The key features of this app are the ability to show the list of running processes in iOS 9 and a jailbreak and security anomaly detection that can help security concerned users to check for potential privacy issues and security threats.
Process List
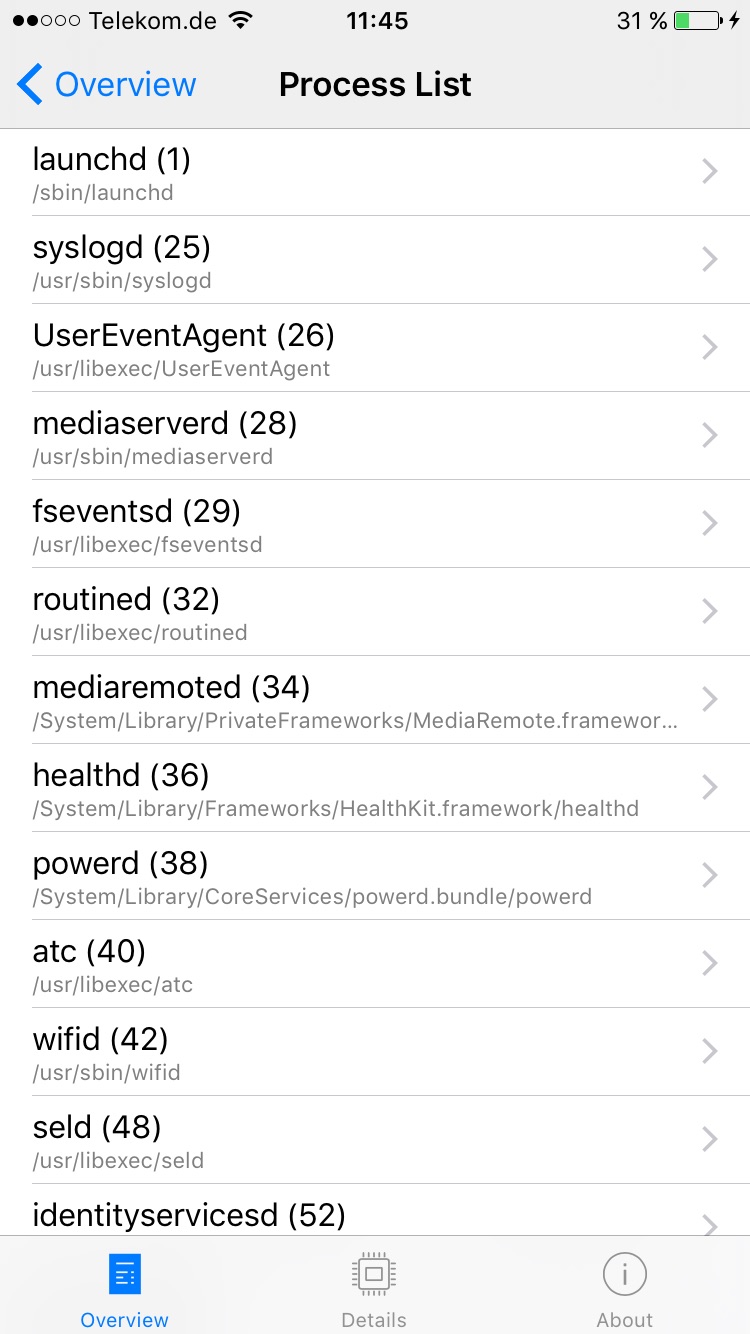
System and Security Info is currently the only app in the Apple AppStore that is capable of showing a list of the running processes in iOS 9. All other system information tools showing the list of running processes ceased to work in iOS 9 because Apple hardened the sandbox to not allow access to querying information about running processes anymore. According to a talk during WWDC 2015 they did this to stop other applications from gathering information about other applications installed on a user's system.
See https://developer.apple.com/videos/play/wwdc2015/703/ "App Detection" starting at 08:34
During this talk they discuss several APIs used to gather information about processes currently running on your system (around 12:12 in the video) and claimed to have fixed them. However as so often Apple has only partially fixed the problems they claim to have fixed. Therefore they have actually never stopped malicious applications from gathering information about what other applications run currently on your device, but only removed access to detail information that is only relevant for harmless system information tools anyway.
System and Security Info is therefore still able to show the list of running processes and enriches this list with information from the codesigning information including the list of entitlements running processes have.
Jailbreak Detection
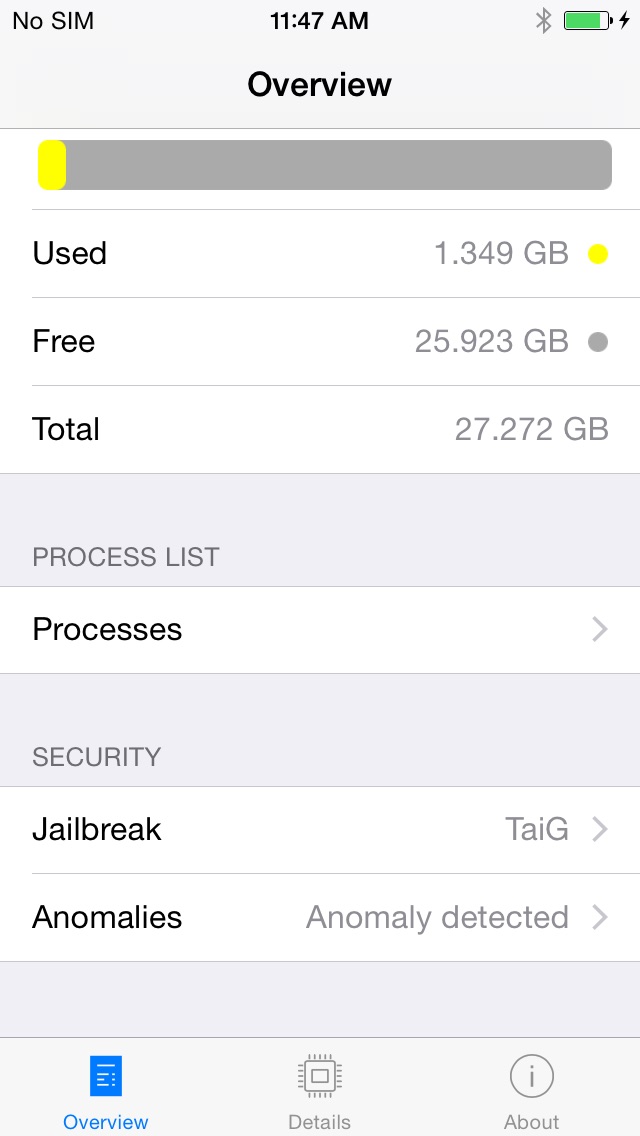
As a company known for iOS kernel and jailbreaking research SektionEins is from time to time asked by concerned iPhone users to determine if their device got hacked or secretly jailbroken to gather information about them. To find this out with a high level of certainty we have to utilize private jailbreak exploits, because Apple locks down iOS devices from both defenders and attackers, which proves to be more often a problem for defenders than for the attackers. This is a costly process. We therefore wanted to provide the public with a low cost solution that allows to find out if someone used one of the public jailbreak or a customized version to hack and backdoor your device. System and Security Info therefore runs a number of tests to determine if it can find artefacts of one of the known jailbreaks and runs further generic tests to determine if e.g. the code signing functionality seems to be still working or not.
DISCLAIMER: Of course such tests in a publicly released tool can never fully replace a detailed analysis in our lab, because attackers can adapt and specifically detect and subvert our tool. They provide however a good first round of checks in the process to determine if the security of your iOS device has been compromised. Furthermore it has been reported that several vendors selling iOS spyware fully rely on modified public jailbreaks for their tools. The chance of detecting one of those is therefore high.
Anomaly Detection
The anomaly detection in this app tries to verify that certain security assumptions are still valid. This includes that code signing flags of running processes have not been tampered with, the app is still encrypted and not running in a debugger and that code signing still detects malicious apps and that no unsigned binaries are running. Furthermore it is validated that no unexpected libraries are injected into the process because this is usually used to tweak runtime functionality. Because the accessibility features of iOS will inject unexpected libraries into our process the app will mention this as a detected anomaly.
Technical Details
Throughout the next weeks we will release several blog posts detailing how the jailbreak and anomaly detections work internally and what it means when they fail on your device.
Privacy and Security
System and Security Info is designed to only show the information gathered to you on your own device. At no point any information is transferred off the device.
Stefan Esser