How to protect yourself with System and Security Info
SektionEins shows a demonstration how "System and Security Info" can help you detect actually happening attacks.
How to protect yourself with System and Security Info

You might have heard about a recent stunt that John McAfee pulled on some reporters to show that he broke the encryption of WhatsApp. In order to execute this hack he sent them phones that contained a backdoored version of WhatsApp.
This is a perfect use case to demonstrate how useful our "System and Security Info" application is that we sold on the iOS AppStore. However if you did not get it by 14th of May you will not be able to get it again, because Apple killed us from the AppStore in their never ending quest to deny that iOS should be allowed to have security tools provided by 3rd parties. Their official statement is that our app was pulled, because the output could confuse our users.
Let's get back at the problem at hand. The average iOS user will likely not be attacked by a government grade stealthy iOS rootkit but instead the usual attacks will occurr: People will trick them into installing enterprise apps or after gaining short time physical access to a device whole apps will be replaced by developer or enterprise signed backdoored apps. This is exactly the type of attack that was in preparation at HackingTeam with their backdoored NewsStand app (which was discovered when all of their data was stolen and leaked to the internet). And this is exaclty the type of attack McAfee tried to use to trick reporters into believing that he broke the WhatsApp encryption. This is at least what the media is reporting about this case.
So how would you detect such an attack with the help of "System and Security Info" (if you were one of the lucky to get it before Apple censored it from the AppStore):
Before you do this test you need to be able to trust our App was not compromised in the same way WhatsApp might have been. So before you do this test you need to freshly reinstall our App. This is usually possible directly from the AppStore if you bought the App before it was pulled.
First open up any app that you want to test on your phone like e.g. WhatsApp.
Now open our app and select "Process List / Processes"
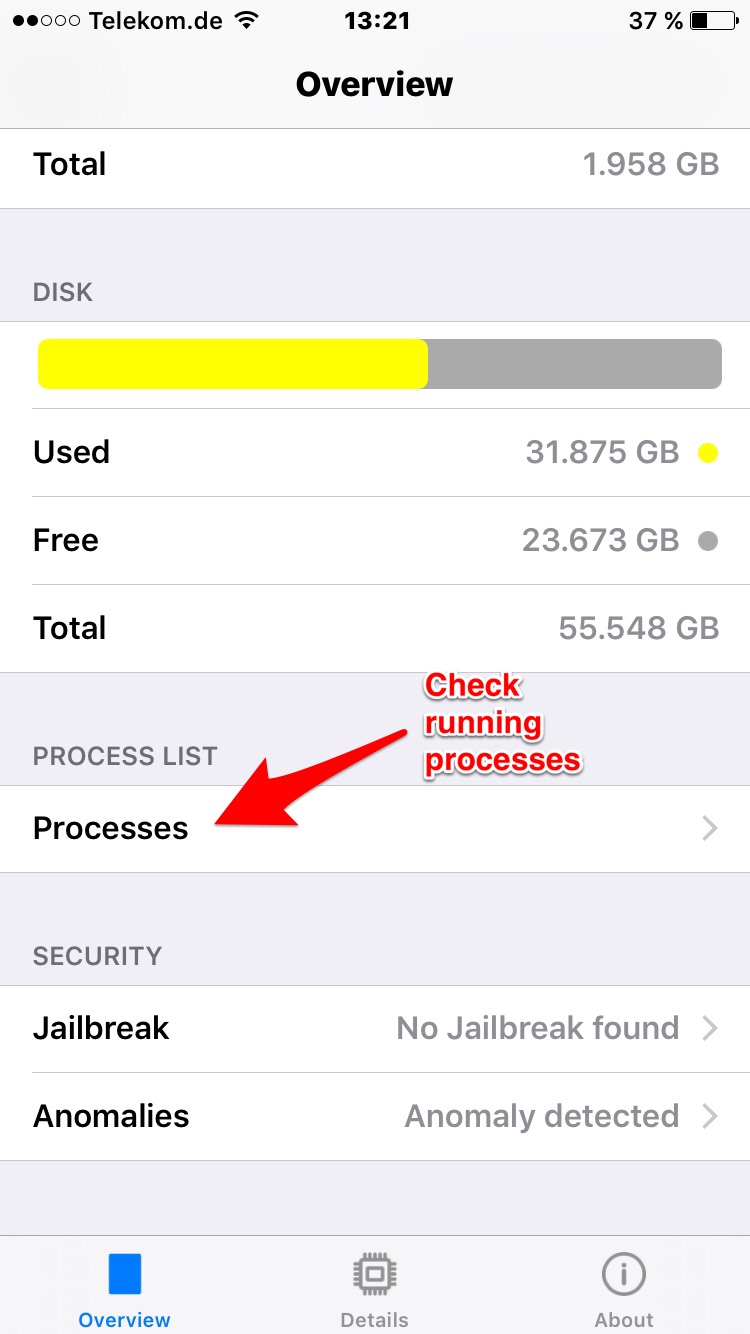
Find WhatsApp in the list of processes
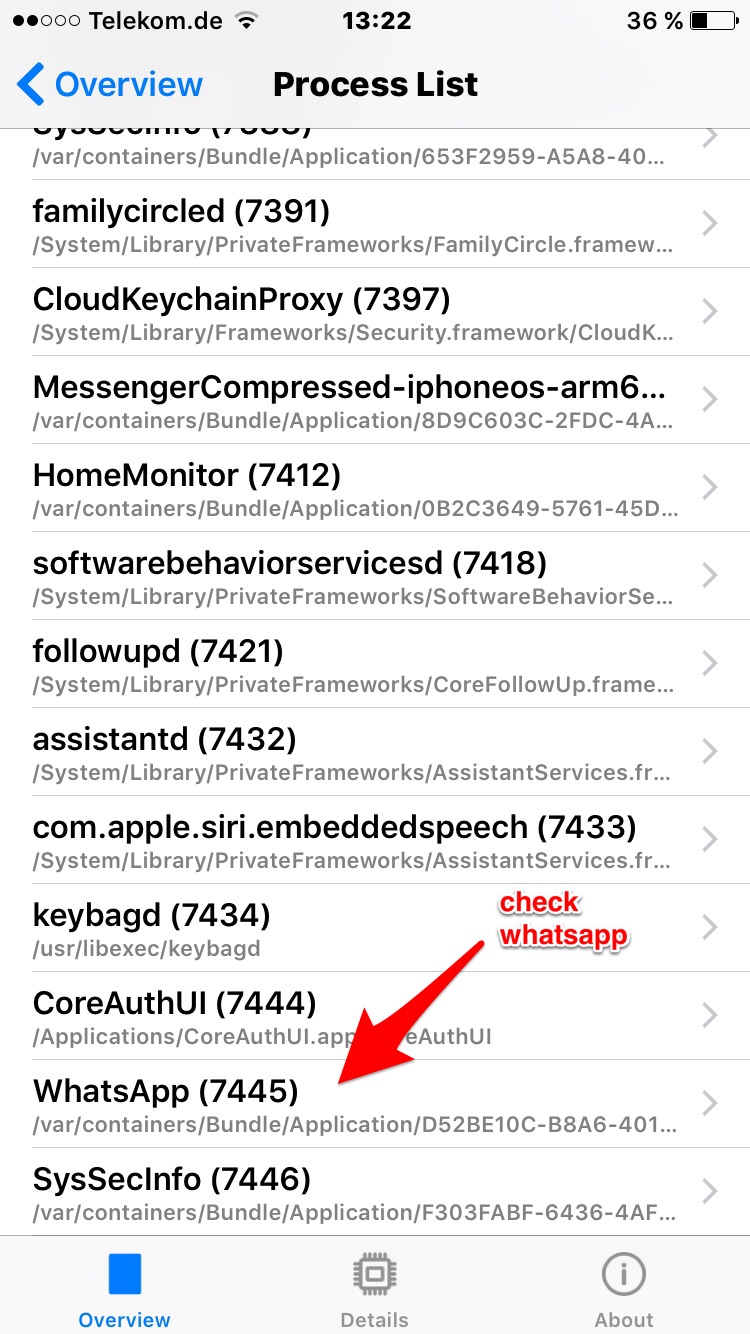
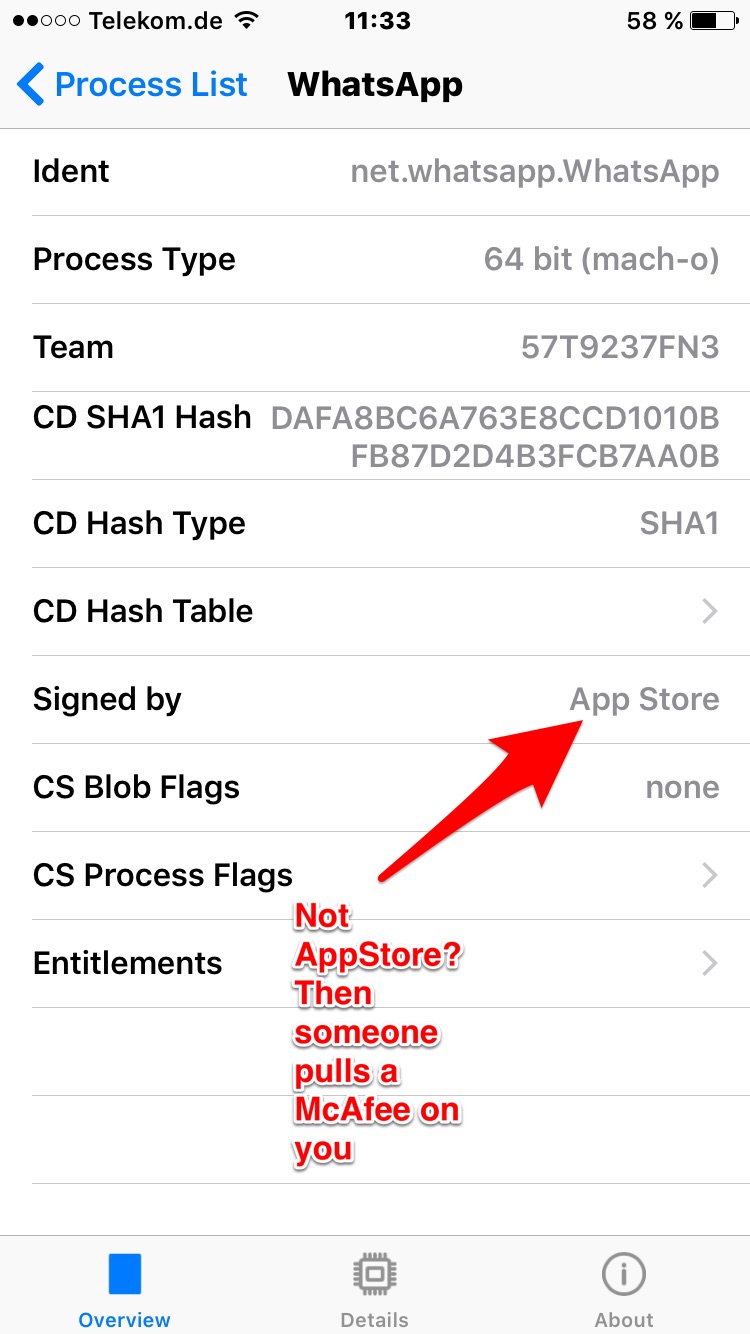
Check if the app reports WhatsApp as signed by the AppStore. If it is no longer signed by AppStore then you might have been backdoored. (Unless your company runs a software that automatically resigns everything you install)
Note: if you want to check that the builtin Apps like NewsStand are not replaced you need to check if our app says "adhoc" (was changed to "builtin" in latest version that we cannot submit to the store anymore).
And I want to thank everyone who bought the application and is concerned about their iPhone's security. We will put the money to good use and use it to finance our future research into iOS security problems.
Stefan Esser